In today's digital age, security threats like phishing attacks have become increasingly sophisticated, making it more challenging for businesses to protect sensitive information. That's where hardware authentication comes in. Hardware authentication involves using a physical token--like a USB drive or key fob--to provide an extra layer of protection beyond traditional login systems. In this blog post, we'll explore the advantages of hardware authentication, including enhanced security, convenience, and protection against phishing attacks. We'll also discuss how hardware authentication works and why it's becoming an increasingly popular choice for businesses looking to safeguard their data.
What is hardware authentication and how does it work?
Hardware authentication is a security solution that involves the use of a physical token, such as a USB drive, key card, or key fob, to provide an additional layer of authentication for users beyond the standard username and password. The token is unique to the user and must be physically present to access their account, adding an extra level of security to the login process.
How does hardware authentication provide an extra layer of security?
Studies reveal that hardware authentication provides a significant security improvement when compared to traditional two-factor authentication (2FA) systems. Unlike 2FA, which relies on a password and a security code sent via phone or email, hardware authentication adds a physical component to the authentication process. This physical token is unique to the user and must be physically present to access their account, providing an extra level of protection.
According to a report by Microsoft, multi-factor authentication (MFA) has been found to reduce the risk of data breaches. However, incorporating hardware authentication into a multi-factor authentication solution can take security protection to the next level. Hardware authentication can also eliminate the need for multiple authentication steps while reducing the risk of phishing attacks. With hardware authentication, even if a customer is tricked into providing their password, the attacker would still need physical access to the user's hardware token to gain access to sensitive digital information. This provides an added layer of security and reduces the risk of data breaches and theft of sensitive information.
What are the advantages of hardware authentication for customers?
Hardware authentication offers a range of advantages to customers, including enhanced security, convenience, protection against phishing attacks, and peace of mind. With the ability to protect against the most sophisticated cyber threats and the convenience of streamlined login processes, hardware authentication is a tool that customers and businesses alike can rely on.
How does hardware authentication offer convenience in the digital age?
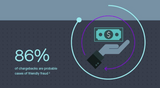
Hardware authentication offers more protection against phishing attacks, a type of cybercrime where unauthorized entities use emails, websites, and other forms of communication to trick users into providing sensitive information. Phishing attacks are a major contributor to corporate security breaches, with approximately 90% of such breaches being the result of these attacks. With hardware authentication, even if a customer is tricked into providing their password, the attacker would still need physical access to the user's hardware token to gain access to sensitive information. This provides an added layer of security and reduces the risk of data breaches and theft of sensitive information.
The convenience of hardware authentication lies in its ability to streamline the login process, eliminating the need for multiple authentication steps. By simply using the physical token, customers can quickly and easily access their accounts while enjoying peace of mind knowing that their information is being kept secure.
In conclusion, hardware authentication is an effective, convenient, and reliable solution for protecting sensitive information in the digital age. By providing an additional factor of security and streamlining the login process, customers can enjoy enhanced security, convenience, and peace of mind.